In Washington state, a group of thieves made headlines when they 3D printed copies of postal master keys, putting more than 73,000 at risk of mail theft. With 3D printers now being more accessible to consumers, criminals are increasingly using the technology for illicit purposes.
Should you be concerned about people 3D printing copies of your business’s keys? Let’s look at the risks and how to address them.
Bad Actors Can 3D Print a Key Using a Photo
To 3D print a copy of keys, someone only needs a photo. In a 2021 research report, researchers describe their experience reverse engineering mechanical keys from pictures. Using an image, they created 3D reconstructions of five different types of keys and printed them. All the duplicated keys succeeded in unlocking tests.
Someone could snap a photo of keys without even being in the same room.
In fact, someone could snap a photo of keys without even being in the same room. In 2008, computer scientists built a software program that could duplicate keys from a photo taken 195 feet away. Using a 5-inch telephoto lens, the scientists stood on the roof of a building and took photos of keys sitting on a table through the window of a nearby café.
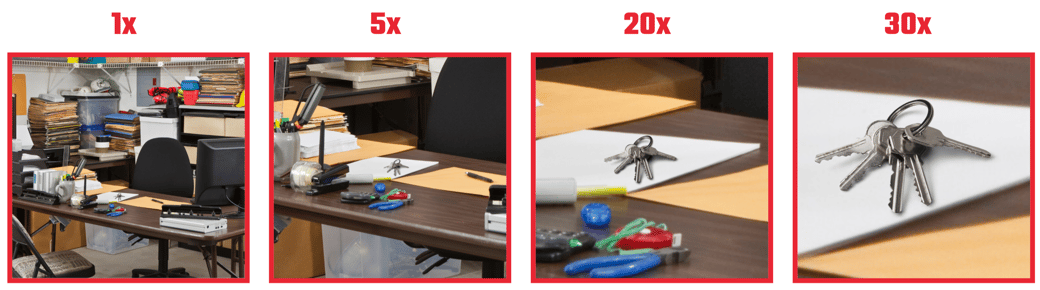
Today, capturing photos from a distance doesn’t require a special lens. There are phones equipped with telephoto cameras featuring zoom capabilities of up to 30x. For reference, a 4x zoom ratio can identify someone 100 feet away. With 20x and 30x zoom ratios, that distance increases to 200 feet and 250 feet, respectively. Imagine how easy it would be for a bad actor to snap a photo of keys an employee had left out on their desk. Once bad actors have a photo of the keys, 3D printing allows them to copy the keys on demand.
3D Printing Is Only One of Multiple Duplication Methods
If someone has a picture of a key, they can still duplicate it without a 3D printer. In 2013, two convicts escaped from an Australian prison using a key replicated from a master key design printed on the cover of the information handbook distributed to all inmates. One of the escapees, a jeweler, had used jewelry-making equipment in his cell to create the key. For someone who isn’t incarcerated, key duplication is a lot easier — there are several online services that will copy a key from a photo.
In addition, while 3D printing has the advantage of on-demand duplication, it’s limited in terms of accuracy and complexity compared to traditional key duplication methods. High-security keys are designed with certain features (e.g., four sets of teeth) to make them difficult to copy. There are even locks designed to thwart 3D printing.
Unauthorized key duplication is the broader risk to your business.
If a bad actor wants to copy a key, 3D printing is only one of the methods available. Unauthorized key duplication is the broader risk to your business.
Effective Key Control Reduces the Risk of Unauthorized Duplication
To address the risk of someone making unauthorized copies of your organization’s keys, implement key control processes and procedures that include the following elements:-1.png?width=800&height=356&name=3D%20PRINTEDgraphic%20(2000%20x%20750%20px)-1.png)
Restricted Access
Store physical keys securely in an electronic key control system to limit the opportunity for someone to remove and copy a key without being noticed. Avoid leaving keys out in the open where they can be photographed for duplication purposes.
Tracking and Accountability
Key control systems ensure only authorized people have access to keys. These systems keep a record of who’s accessed keys and when they were issued or returned. This accountability discourages individuals from attempting to duplicate keys because their actions are traceable.
Regular Auditing
Periodic audits of key inventory ensure that all keys are accounted for and that none are missing. If a key goes missing, this audit trail can be crucial in identifying the source of the security breach and taking appropriate action.
Security Awareness and Training
Educate employees about the importance of safeguarding physical keys and the risks associated with leaving keys out in the open. This awareness can lead to increased vigilance and responsible key handling.
Physical Security
Key control systems are typically part of a broader physical security strategy that includes measures like surveillance cameras and alarms. These precautions deter people from misusing or stealing keys.
While key control measures can’t guarantee someone won’t duplicate a key, a comprehensive security strategy reduces your organization’s overall risk.
As bad actors get more creative with using 3D printers, the risk of them printing copies of your business’s keys is a legitimate concern — but it’s not a new issue. By proactively addressing the overall threat of unauthorized duplication, you can protect your organization against potential breaches.


