Spring cleaning isn’t just for tackling that one junk drawer in your desk or clearing out your inbox — it’s also the perfect time to refresh your key control processes. Proper maintenance keeps your KeyTrak system running smoothly and your keys secure, while improving productivity. Not sure where to begin? Start with these 10 tasks.
1. Tidy Up Your Key Control Area
Take some time to declutter and organize your key control space. A tidy area makes it easier for people to use the system and reduces the risk of lost or misplaced keys.
2. Clean Your System
Regular cleaning and disinfecting promote a healthier environment for system users. To do so, follow these steps:
- Dampen a clean, lint-free cloth with a 70% isopropyl alcohol solution. Use only nonabrasive cloths, and avoid the cleaners listed in the graphic below.
- Squeeze out excess moisture to prevent liquid from dripping into the system. If liquid gets inside, contact us ASAP for guidance.
- Disinfect the surfaces, avoiding the fingerprint reader. Allow the system to air dry before using it again.
- Clean the fingerprint reader by pressing office tape to the surface and lifting it to trap oils and clear the scanner. You can also use a soft, dry cloth. Complete this step about once a week.

3. Audit Keys
To identify any key control discrepancies, conduct a key audit involving the following steps:
- Look for overdue or unreturned keys.
- Check for any loose keys that need to be tagged and added to the system.
- Update key descriptions in your system as needed.
- Review long-term key assignments to see if any updates are required.
- Document missing or damaged keys.
- Analyze key usage patterns for security concerns.
4. Review Users
Inactive or outdated user accounts are a significant security risk. Review your users and complete these maintenance tasks:
- Deactivate inactive users, whether they’re former employees or staff members who no longer require key access.
- Verify personal data, such as home address and driver’s license number and expiration.
- Update access permissions. Make sure each user’s access permissions reflect their job responsibilities. To make this process more manageable, consider auditing employees by department.
- Reassess user roles. These are specific permissions you set up for certain types of job roles, like porter or manager, and can assign to specific users. Make sure each role and its settings are still appropriate.

To update a user's personal information or access levels, go to Data Maintenance > Users and then select the pencil icon for the user you'd like to edit.
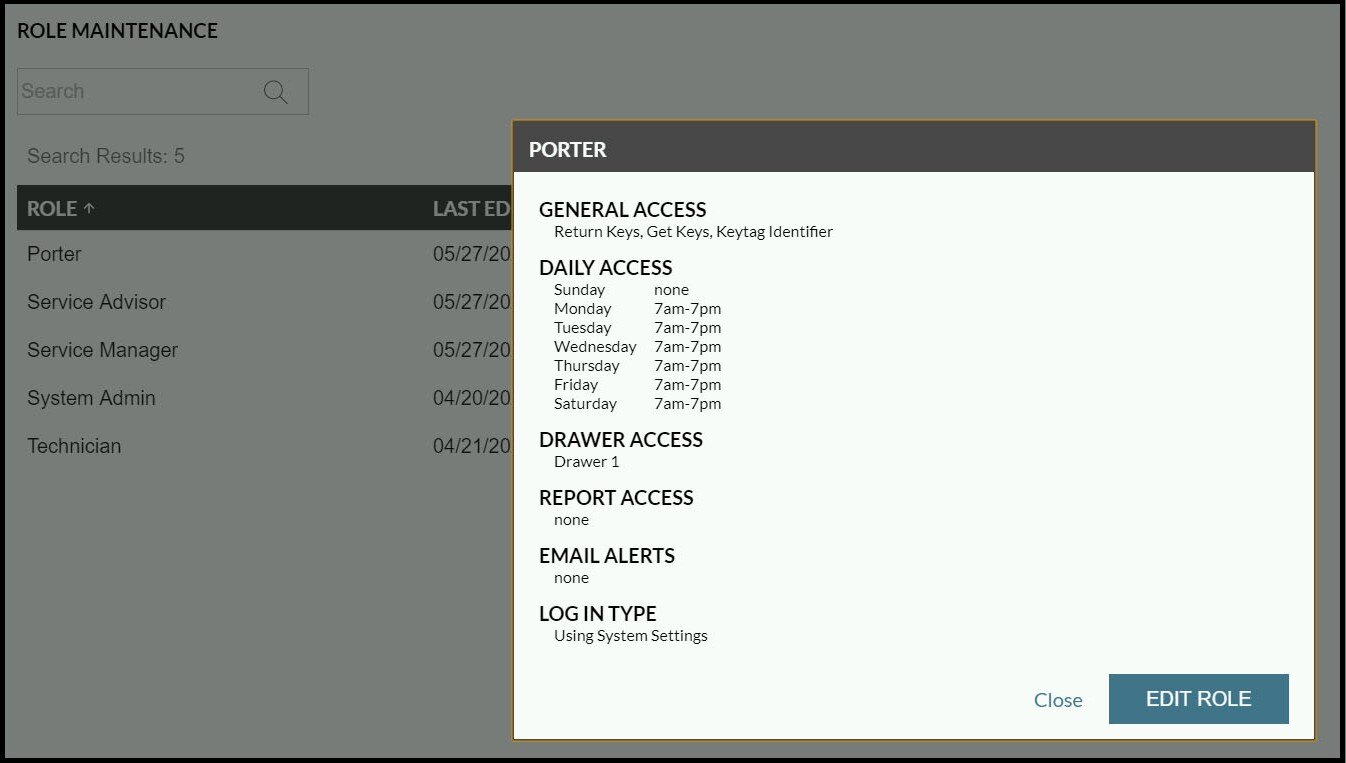
To manage user profiles, navigate to Administration > User Roles. To edit a role, select the corresponding pencil icon.
5. Evaluate System Notification Settings
Take a few minutes to look at system alarms and notifications. Confirm you’ve selected the desired alarm triggers, such as unauthorized key removals, overdue keys, or open drawers. Also, make sure text or email alerts are going to the right people.
In addition, check your Auto Run reports to ensure the appropriate people are getting timely updates on key usage.
6. Update Passwords and PINs
Regularly updating passwords is one of the most basic principles of digital hygiene, so make sure users are keeping theirs current. Setting time limits on passwords can help enforce this best practice.

To change the password settings in your system, navigate to Administration > System Configuration and select the Passwords button.
| TIP: Make sure your PIN isn’t one of the top 50 PINs to avoid. |
7. Ensure Software Is Up to Date
Having updated software is essential for security patches and new features. Verify your system is running the latest version. If you have questions about your software version, contact our support team.
8. Verify Your Data Backups
Make sure your KeyTrak system data is backed up in case of a power outage or other disaster. If you have KeyTrak Cloud Backup, your data will be backed up automatically each night. If you use external backups:
- Confirm your system is set to back up daily.
- Store backup files on an external device.
- Ensure the Tag Inventory report is included in your backup.
 The Tag Inventory report displays a list of key tags and their positions in the KeyTrak drawer.
The Tag Inventory report displays a list of key tags and their positions in the KeyTrak drawer.
9. Update Key Control Documentation
Review all key control documentation to see if any updates are required. These documents might include:
- Emergency and disaster recovery procedures
- Key control policy
- Keyholder agreements
- Training documents
10. Replenish Tagging Supplies
Take stock of your tagging supplies and replenish items running low. To order, log into our online supplies catalog or call 800.541.5033 (select option 2).
| TIP: Take a look at our top 10 supplies to see if there’s anything you’re missing. |
Just as a clean desk and empty inbox jumpstart your productivity, fine-tuning your key management will enhance your organization’s security, operations, and efficiency.

%20NEW-1.png?width=2000&height=600&name=Phone%20Notif%20(2000%20x%20600%20px)%20NEW-1.png)